How to Use Chisel for Reverse Tunneling
TL;DR:
Need to display a target's internal app on your own browser? Chisel is a fast TCP/UDP tunnel, transported over HTTP. It is used to bypass firewalls and establish reverse tunnels.
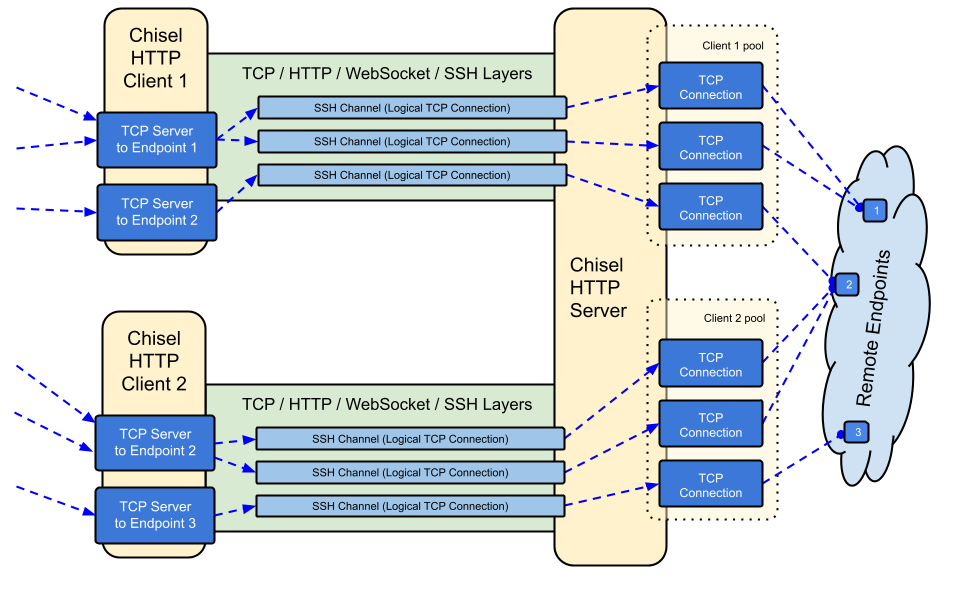
Chisel is a fast TCP/UDP tunnel over HTTP, secured via SSH. It’s a simple tool often used for creating secure tunnels to forward ports or access internal networks from external systems. Chisel supports reverse tunneling, making it particularly useful for penetration testing, remote administration, and secure communications.
Key Features
- Port Forwarding: Forward traffic from a local port to a remote port and vice versa.
- Reverse Tunneling: Connect to internal systems from an external network.
- Cross-Platform: Works on Linux, macOS, and Windows.
- Lightweight: Minimal dependencies and simple to set up.
- Encryption: Secure tunneling over HTTP.
How Chisel Works
Chisel consists of two components:
- Server: Runs on the machine exposed to the network and listens for incoming client connections.
- Client: Connects to the server and sets up tunnels for forwarding traffic.
Chisel uses a reverse tunneling mechanism to allow the client to expose its own ports, even if it's behind a NAT or firewall.
When to Use Chisel
- Access Internal Applications: Forward ports from a remote machine to access internal applications.
- Bypass Firewalls: Tunnel through firewalls using HTTP-based traffic.
- Penetration Testing: Access internal services during engagements.
- Remote Access: Securely manage machines behind NAT or firewalls.
Practical Scenarios
- Exposing a Web Application: A web server running on an internal machine can be accessed remotely by forwarding its port.
- SSH Reverse Tunneling Alternative: Use Chisel in environments where SSH tunneling is blocked.
- Proxying HTTP Traffic: Intercept and forward HTTP traffic securely for analysis.
Prerequisites
- Server Machine:
- Chisel installed or binary available.
Publicly accessible IP address (e.g.,
10.10.14.46).Client Machine:
- Chisel installed or binary available.
Access to a local or restricted service you want to tunnel.
Network:
- Ensure the client can reach the server on the specified port.
Setup
We’ll create a reverse tunnel where a local service running on the client machine will be accessible from the server machine.
Kali Linux
Yes! You can easily install Chisel directly on Kali Linux using the package manager. Here's how:
Installing Chisel on Kali Linux
- Update Your Package List:
Run the following command to ensure your package list is up-to-date:
sudo apt update
- Install Chisel:
Install the Chisel package using:
sudo apt install chisel
- Verify the Installation:
Check if Chisel is installed correctly:
chisel version
You should see the installed version.
Using the Installed Chisel
Once installed, you can use Chisel for both server and client roles without needing to download binaries manually:
- Start the Server:
chisel server --reverse --port 9000
- Connect as a Client:
chisel client <server-ip>:9000 R:<local-port>:<target-ip>:<target-port>
For example:
chisel client 10.10.14.46:9000 R:8080:127.0.0.1:8080
Other Linux Systems
This method is simpler and avoids handling binaries manually if you're using any Debian-based distribution.
Steps
Step 1: Download and Install Chisel
- On both client and server, download Chisel from the official GitHub releases page.
- Choose the appropriate binary for your OS and architecture.
# Example for Linux 64-bit
wget https://github.com/jpillora/chisel/releases/download/v1.10.1/chisel_1.10.1_linux_amd64.gz
gzip -d chisel_1.10.1_linux_amd64.gz
chmod +x chisel_1.10.1_linux_amd64
mv chisel_1.10.1_linux_amd64 /usr/local/bin/chisel
Verify installation:
chisel version
Step 2: Start the Chisel Server
- Start the Chisel server on the server machine in reverse mode.
chisel server --reverse --port 9000
- Output Example:
2024/12/04 11:48:17 server: Reverse tunnelling enabled
2024/12/04 11:48:17 server: Listening on http://0.0.0.0:9000
Step 3: Start the Chisel Client
- On the client machine, connect to the server and establish the reverse tunnel.
./chisel client <server-ip>:9000 R:<local-port>:<target-ip>:<target-port>
For example, to forward a local service on 127.0.0.1:8080 to the server:
./chisel client 10.10.14.46:9000 R:8080:127.0.0.1:8080
- Output Example:
2024/12/04 11:48:29 client: Connected (Latency 12ms)
Step 4: Access the Tunnel
- On the server machine, access the forwarded service using the server's localhost and the forwarded port.
curl http://127.0.0.1:8080
Alternatively, open the browser and navigate to:
http://127.0.0.1:8080
Use Cases
- Access Restricted Services:
Forward internal services running on the client to the server.
Pentesting and Red Teaming:
Bypass network restrictions to access internal assets.
Remote Administration:
- Manage a system behind NAT or firewalls.
Troubleshooting
- Port Already in Use: Ensure the port used for the server (
9000) and client (8080) is not in use. - Connection Issues: Check network connectivity between client and server. Also, ensure the server IP and port are correct.
- Permission Issues: Ensure the Chisel binary has executable permissions (
chmod +x). Debugging:
Use
-v(verbose) for debugging:
./chisel client -v 10.10.14.46:9000 R:8080:127.0.0.1:8080
Advanced Usage
- Multiple Ports:
Forward multiple services by chainingRoptions:
./chisel client <server-ip>:9000 R:8080:127.0.0.1:8080 R:8443:127.0.0.1:8443
- UDP Tunneling:
Forward UDP traffic:
./chisel client <server-ip>:9000 U:53:127.0.0.1:53
- Authentication:
Use authentication for added security:
chisel server --reverse --port 9000 --auth username:password
./chisel client <server-ip>:9000 R:8080:127.0.0.1:8080 --auth username:password
Final Words
Chisel is a powerful tool for creating reverse tunnels and accessing restricted services. By carefully configuring the server and client, you can effectively bypass network restrictions and securely access internal services.
Latest Comments
Sign in to add a commentNo comments yet. Be the first to comment!